
Dirty App Removal: Trigona Ransomware
Ransomware continues to evolve into one of the most dangerous forms of malware, and Trigona is no exception. A recent variant, Trigona ransomware, encrypts files and appends the “._locked” extension to them, making it impossible for victims to access their important data without paying a ransom. But as we’ll explore in this post, paying that ransom isn’t always a guarantee of recovery.
What Is Trigona Ransomware?
Trigona ransomware is a notorious malware that infiltrates systems, encrypting files and appending the extension “._locked” to them. For instance, a file named “1.jpg” will be renamed to “1.jpg._locked” after encryption, making the data inaccessible. This encryption process also embeds a unique decryption key and victim ID into each file, which the threat actors use to demand payment in exchange for restoring the data.
Automatically Detect and Remove Ransomware Threats from Your Computer with SpyHunter
Is Your Computer Infected with Ransomware? Automatically Remove Ransomware Threats for FREE and Protect Your Computer with SpyHunter.
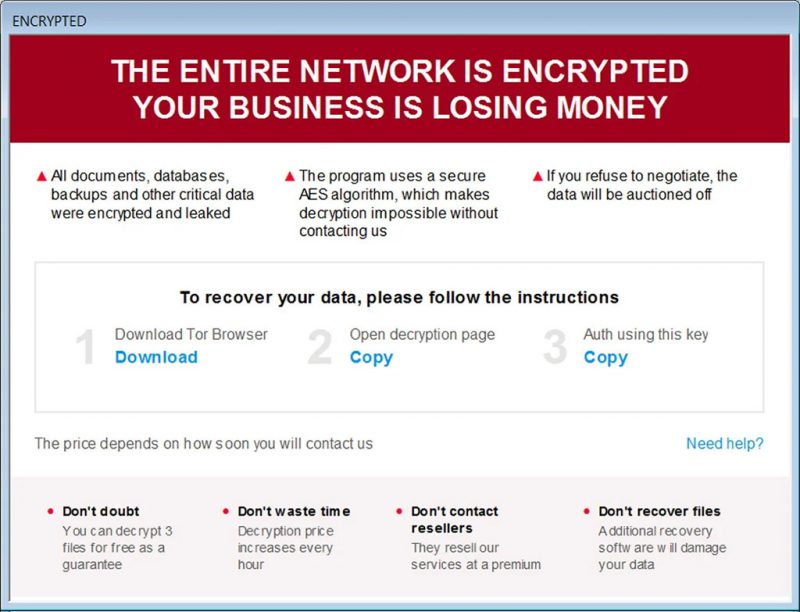
The infection leaves behind a file named “how_to_decrypt.hta,” which serves as the ransom note. This note explains the grim reality: not only has your data been encrypted, but it has also been leaked. Victims are told that unless they pay a ransom, their personal information will be sold to third parties. Even more threatening, the ransom price increases hourly, creating pressure to act quickly.
However, what the criminals don’t mention is that even if you pay, there’s no guarantee you’ll regain access to your files. Many victims have paid only to be left with encrypted data and no way to recover it.
The Trigona Ransomware note reads like the following text:
THE ENTIRE NETWORK IS ENCRYPTED
YOUR BUSINESS IS LOSING MONEY
All documents, databases, backups and other critical data were encrypted and leaked
The program uses a secure AES algorithm, which makes decryption impossible without contacting us
If you refuse to negotiate, the data will be auctioned off
To recover your data, please follow the instructions
Download Tor Browser
Open decryption page
Auth using this key
The price depends on how soon you will contact us
Need help?
Don’t doubt
You can decrypt 3 files for free as a guarantee
Don’t waste time
Decryption price increases every hour
Don’t contact resellers
They resell our services at a premium
Don’t recover files
Additional recovery software will damage your data
Why Is Ransomware So Dangerous?
Ransomware is one of the most damaging forms of malware, primarily because it targets what people value most: their data. Whether it’s personal photos, business documents, or entire databases, the loss of these files can cripple individuals and organizations alike.
Once infected, the malware spreads rapidly, encrypting as many files as it can. Worse yet, if the infected computer is connected to a network, the ransomware can extend its reach, encrypting files on other connected devices.
In the case of Trigona, the threat goes beyond simple file encryption. The attackers also claim to leak stolen data, turning a ransomware infection into a full-scale data breach. This dual threat of data loss and exposure leaves victims with few options—none of which are ideal.
How Does Ransomware Like Trigona Infect Computers?
Cybercriminals are constantly devising sneaky methods to spread ransomware. Here are a few common ways your computer might become infected:
- Spam Emails: Phishing emails are a primary method of delivering ransomware. These emails often contain malicious attachments or links that look legitimate but trigger infection once clicked.
- Cracked Software: Downloading cracked or pirated software from shady websites often leads to malware infection. Cybercriminals use these websites as distribution hubs for ransomware.
- Unreliable Websites: Visiting websites that host untrustworthy downloads, such as free file-sharing platforms or third-party downloaders, significantly increases the risk of infection.
- Trojans and Fake Updates: Hackers often disguise ransomware as system updates or harmless programs. Once downloaded, the ransomware silently begins encrypting files without the user’s knowledge.
Once ransomware is in your system, it begins its malicious process, locking files and making them inaccessible without the required decryption key—which only the attacker has. Even more alarming, it can spread across local networks, affecting multiple systems and compounding the damage.
Preventing Ransomware Infections
Luckily, there are steps you can take to protect yourself from ransomware like Trigona:
- Only Download Software From Trusted Sources: Avoid using P2P networks, third-party downloaders, or shady websites that may host malicious software. Stick to official websites and verified app stores.
- Keep Your System Updated: Outdated software is a common vulnerability exploited by ransomware. Regularly update your operating system and applications to ensure you’re protected against the latest threats.
- Use Anti-Malware Software: Running regular scans with a trusted anti-malware program can help detect threats before they cause serious damage. Programs like SpyHunter can automatically detect and eliminate ransomware infections.
- Be Cautious With Emails: Always be cautious when opening emails from unknown sources, especially if they contain attachments or links. Even if the email looks legitimate, it could be part of a phishing attempt designed to spread malware.
What To Do If You’re Infected with Trigona Ransomware?
If you find yourself the unfortunate victim of Trigona ransomware, it’s critical to act fast. Here’s what you should do:
- Disconnect From The Network: Immediately disconnect your computer from any networks to prevent the ransomware from spreading to other devices.
- Do Not Pay the Ransom: As tempting as it may be, paying the ransom does not guarantee that you’ll get your data back. Many victims pay only to be scammed by cybercriminals who never deliver the decryption key.
- Run an Anti-Malware Scan: Use trusted anti-malware software, such as SpyHunter, to scan and remove Trigona ransomware from your computer. Once removed, you can focus on recovering your files.
Unfortunately, once ransomware has encrypted your data, it’s challenging to recover without the decryption key. The best-case scenario is that you have a recent backup of your files that you can restore after removing the ransomware.
Protecting Yourself Against Ransomware
Ransomware like Trigona is a constant threat in today’s digital landscape. By being cautious and practicing good cyber hygiene, you can greatly reduce the risk of infection. However, no protection method is foolproof. Therefore, it’s crucial to regularly back up your files, keep your software updated, and use reliable anti-malware tools to scan for potential threats.
If your system is already infected with Trigona ransomware, we strongly advise using a reputable anti-malware tool like SpyHunter to eliminate the threat immediately. Remember, prevention is the best cure when it comes to ransomware attacks.
HOW TO REMOVE RANSOMWARE
Automatically Detect & Remove Ransomware Threats for FREE with SpyHunter.